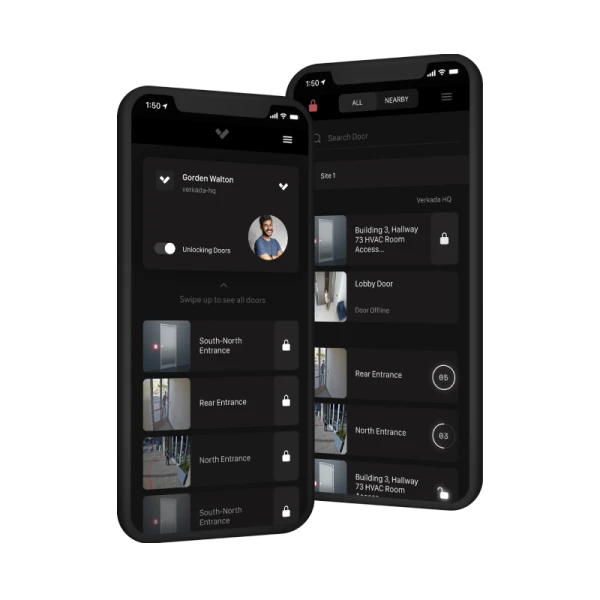
Cloud Based Access Control
Office access control is a system that restricts access to certain areas of an office building or workplace. It can be used to protect sensitive information, equipment, and assets, as well as to deter theft and vandalism. Office access control systems can be as simple as a lock and key system, or as complex as a biometric system that uses fingerprints or facial recognition to identify authorized users.
IP mounted access control units can be used to control access to individual offices, as well as to common areas such as lobbies, conference rooms, and server rooms. They can also be used to control access to different levels of a building, such as restricted areas for executives or confidential information.




Enhanced Security and Visibility
- Remote Monitoring & Management: Cloud-based access control provides real-time visibility into who is entering your facility and when, helping enhance situational awareness and response capabilities.
- Data Encryption: Communications are secured using industry-standard encryption protocols (such as TLS 1.2), safeguarding sensitive information during transmission.
- Tamper Detection: Built-in sensors can detect unauthorized attempts to access or alter the system, triggering alerts to prevent potential breaches.
Flexible Installation and Scalability
- Versatile Deployment: Systems are designed to function in a variety of environments including indoor, outdoor, metal, and non-metal door setups.
- Easy Setup: Devices can often be configured quickly using mobile applications, reducing setup time and complexity.
- Efficient Wiring: Many solutions utilize Power over Ethernet (PoE), which simplifies installation by using a single cable for both power and data, reducing the need for additional electrical work. leverage current networks without major upgrades.
Operational Efficiency
- Local Mode Capabilities: Local processing enables faster response times and minimizes network load, improving overall system performance.
- Seamless Integration: Cloud systems can integrate with existing IT infrastructure, allowing businesses to leverage current networks without major upgrades.
User Convenience and Future-Proofing
- Customizable Inputs: Systems support various functions such as door position monitoring, request to exit, and auxiliary sensors, offering greater control and customization.
- Mobile and Smart Credential Support: Support for technologies like Bluetooth and NFC enables a smoother transition to mobile access credentials, improving user convenience.
- Credential Compatibility: Many cloud solutions are designed to maintain compatibility with existing credential systems, easing the migration process and protecting prior investments.


